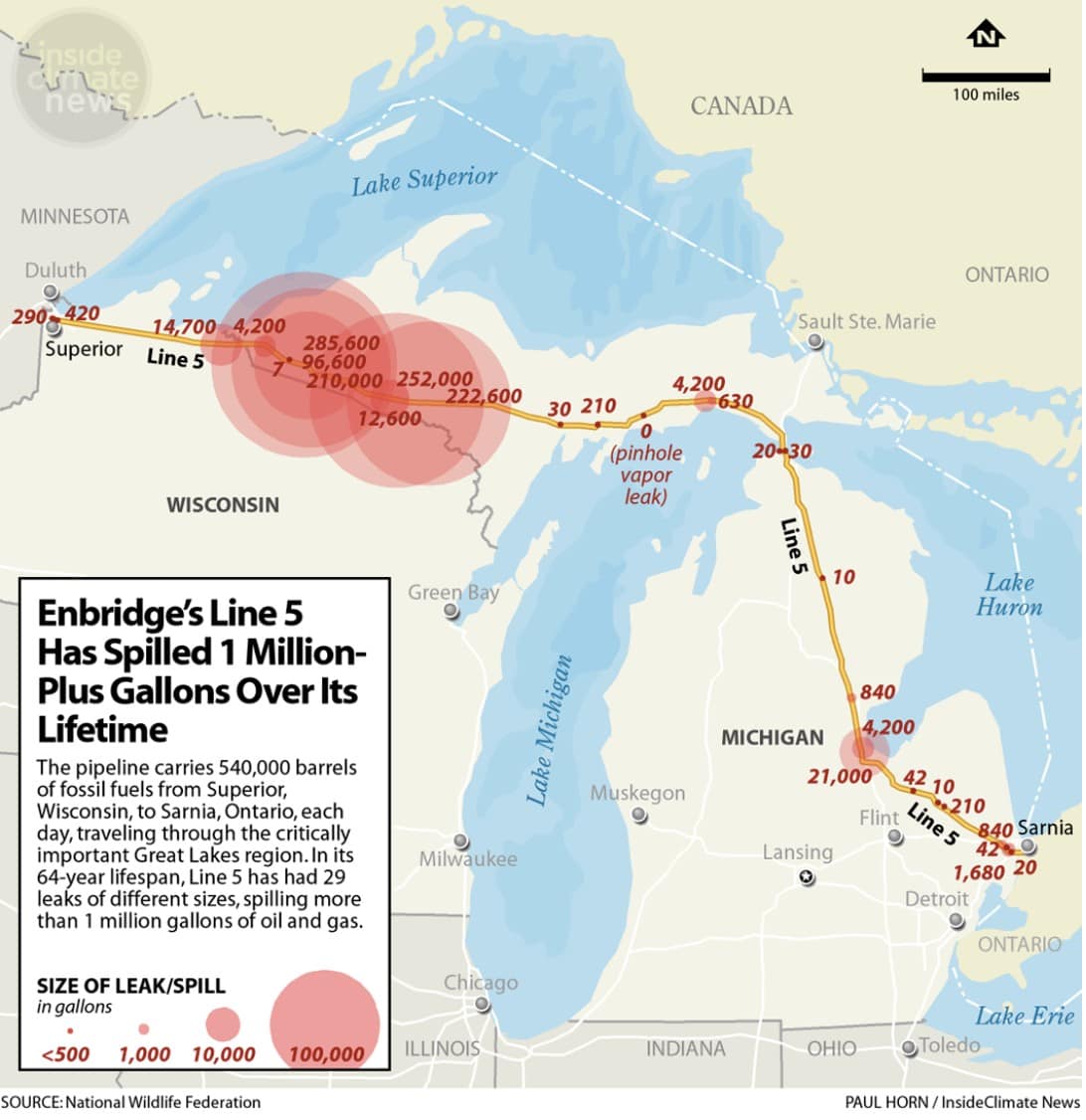
OKEMOS – This has been a busy few
months inside the Washington, D.C., Beltway for policy topics related to
cybersecurity. President Obama signed an executive order in February regarding the
promotion of private-sector information sharing. The U.S. Congress is now
debating several bills, as both sides of the political aisle agree that
addressing cybersecurity is an urgent issue.
According to TheHill.com: “President Obama recently called
cyberattacks a national emergency,” and the cybersecurity legislation has
moved through the Republican-controlled Congress relatively quickly because
leaders from both political parties recognize that cybercrime threatens us all
in a very big way. Now.”
So what are the cyberpolicy initiatives and will new laws be enacted?
Back in late April, the House of Representatives passed the Protecting
Cyber Networks Act by a wide margin of 307-116, with the support of
the White House.
H.R. 1560 would establish within the Office of the Director of National
Intelligence (ODNI) a center that would be responsible for analyzing and
integrating information from the intelligence community related to
cyberthreats. In addition, the bill would require the government to establish
procedures for sharing information and data on cyberthreats between the federal
government and nonfederal entities. CBO estimates that implementing the bill
would cost $186 million over the 2016-2020 period, assuming appropriation of
the estimated amounts.
USNews.com reported that “the bill would offer
legal protections to companies that would enable them to share more information
about their networks and hacker threats with the government.”
Critics of previous bills, such as Rep. Adam Schiff of California, the ranking
Democrat on the House Permanent Select Committee on Intelligence, announced
their support for this bill. Rep. Smith also announced that privacy protections
are stronger in this bill, but cautioned that “improvements may still be needed
to be made to make sure companies are not given too much immunity if they share
unnecessary customer data or if they fail to act on leads about hacker
threats.”
Nevertheless, the bill still has several controversial components. “The use of
defensive measures without appropriate safeguards raises significant legal,
policy, and diplomatic concerns and can have a direct deleterious impact on
information systems and undermine cybersecurity,” the White House said in a statement.
Another bill, H.R. 1731 or “The National Cybersecurity Protection Advancement
Act (NCPA) of 2015,” was introduced in April by two House Republicans from
Texas. The authors, U.S. Rep. Michael McCaul, R-Texas, chairman of the
Committee on Homeland Security, and U.S. Rep. John Ratcliffe, R-Texas, chairman
of the Subcommittee on Cybersecurity, Infrastructure Protection and Security
Technologies, introduced the act to improve cybersecurity by encouraging
voluntary information-sharing about cyberthreats between and among the private
sector and government.
According to the sponsors, the NCPA Act bolsters our nation’s cybersecurity by
providing the liability protections industry needs and the privacy protections
Americans demand and deserve. They wrote: “This pro-security, pro-privacy bill
is the result of close collaboration with industry and privacy stakeholders and
other committees in the House.”
CISA
2015
Meanwhile, over in the U.S. Senate,
the Cybersecurity Information Sharing Act of 2015 (or CISA) passed the Senate
Intelligence Committee in March 2015 by a 14-1 vote. That bill was essentially
the same as CISA 2014, with provisions such as:
Liability Protection. CISA provides strong liability
protection for information sharing that follows CISA�s procedures – so long as
such sharing is not grossly negligent or an act of willful misconduct. Such a
high bar of protection ensures that companies that share or receive information
will not be sued for merely trying to improve their and other’s cybersecurity.
A lower standard, such as “good faith,” may sound strong, but it is much easier
for a tort lawyer to insinuate a lack of good faith than it is to prove willful
misconduct or gross negligence. Overall, this level of liability protection
will ensure that information sharing is less hindered by the threat of
potential lawsuits.
Similarly, CISA provides Freedom of Information Act protections for shared data
and does not allow regulators to use information to directly regulate the
lawful activities of sharers or receivers of threat information.
Authorized Uses. CISA allows the government to use information
gained by information sharing for several purposes, including:
� Enhancing cybersecurity,
� Identifying a cyberthreat from a foreign adversary or terrorist,
� Preventing or prosecuting cases involving death, serious
bodily harm, or other violent felonies,
� Stopping or mitigating threats of serious economic harm,
� Combatting serious threats to minors,
� Investigating and prosecuting cases of fraud and identity
theft, and
� Protecting the U.S. from and taking action against those
who engage in espionage and the theft of trade secrets.
But opponents of CISA 2015 say it still threatens civil liberties and won�t
help win our cybersecurity battles. An ACLU blogger wrote, “CISA is one of those
privacy-shredding bills in cybersecurity clothing.” The blog said that the bill
is all about NSA surveillance.
Bipartisan
Support & Familiar Opposition: But Is This Year Different?
There has been a rare bipartisan unity
in the Congress on these legislative efforts regarding cybersecurity, as well
as general support from the White House, which has been missing in previous
years. Recent press releases have been issued, such as this one from Congressman Cramer who represents North Dakota,
which proclaim that these new cyber bills protect privacy while cracking down
on cybercrime.
“Americans’ personal and financial information is under increasing risk. It’s
estimated that $445 billion per year is lost to cybercrime across the
world. As our reliance on information technology steadily grows, Congress
needed to act to improve the security of our personal and financial information
and ensure confidence. These bills strike the right balance between
protecting an individual�s civil liberties and providing network security
personnel the information they need to protect their networks from future
attacks,” said Cramer.
USA Today commented on Obama�s call for
legislation to help share cyberthreat information between the public and
private sectors.
President Obama has called on Congress to pass strong cybersecurity
information-sharing legislation, and lawmakers have been moving quickly to do
that.
Both the House-passed bill and the bill approved by the Senate intelligence
committee offer liability protection to companies to shield them from lawsuits
that could arise from the sharing of business records with the government and
with one another. Businesses have been reluctant to tell the government about
cyberattacks because of their fear of lawsuits from consumers or privacy
groups.
One key difference between the two bills is that the Senate bill requires
any information shared by private companies to first go through the Department
of Homeland Security. The House bill would allow companies to share their
cyber-threat information with any civilian agency. A bank, for example, could
go straight to the Treasury Department for help.
More
on Privacy Group Opposition
Nevertheless, many critics remain
who oppose these latest legislative efforts. Leo
King at Forbes.com wrote that the cybersecurity law is ridiculously
out of touch.
Earlier this week some 55 civil society organizations and security experts –
including Access, the American Civil Liberties Union, the Bill of Rights
Defense Committee, the Center for Democracy and Technology, Electronic Frontier
Foundation, Human Rights Watch, Liberty, and professors and experts at the
Massachusetts Institute of Technology, Stanford University, the Tor Project,
Twitter and VMware – all expressed incredibly serious concern about the PCNA.
In a letter, they wrote that the act would authorize
companies to monitor users’ online activities, and share information including
their online communication, without proper privacy protection.
A reluctant viewpoint was also articulated by Wired magazine’s coverage of these
cyberbills. After reporting that the Obama administration has announced general
support for these bills, and describing some of PCNA’s significant privacy
safeguards, Wired goes on to quote Robyn Greene, policy counsel for the
Open Technology Institute (OTI).
But privacy advocates haven’t given up on a presidential veto. A new website
called StopCyberspying.com launched by the internet freedom group Access, along
with the EFF, the ACLU and others, includes a petition to the President to
reconsider a veto for PCNA, CISA and any other bill that threatens to widen
internet surveillance.
OTI’s Greene says she’s still banking on a change of heart from Obama, too. “We�re hopeful that the administration would veto any bill that doesn�t address
these issues,” she says. “To sign a bill that resembles CISA or PCNA would
represent the administration doing a complete 180 on its commitment to protect
Americans’ privacy.
Newamerica.org went even further in outlining
their opinion that the Cybersecurity Information Sharing Act of 2015 is
Cyber-Surveillance and not cybersecurity. “Despite increasing doubts about
whether information-sharing legislation could have prevented an Anthem, Sony or
Home Depot-style hack, CISA’s proponents insist that passing cybersecurity
information sharing legislation is the single most important way to enhance
cybersecurity. However, the bill’s primary effect will be to increase
cyber-surveillance.”
The overall privacy argument against NSA appeared to be helped a bit last week
when a federal appeals court in Manhattan Thursday
struck down the government’s controversial National Security Agency program to
collect bulk data on Americans’ telephone calls.
“The judges permitted the NSA program to continue temporarily as it exists, but
they implored Congress to better define where boundaries exist or risk invasions of privacy unimaginable in the past.”
Progress
in Information Sharing on the Ground?
Beyond efforts on Capitol Hill on
new legislation, there has also been movement toward implanting the new
information sharing organizations promised by the president�s executive orders
on cybersecurity earlier this year.
In his PwC blogs, David Burg laid out next steps in cybersecurity
information sharing. He describes how: “Information Sharing and Analysis
Organizations (ISAOs) have the potential to energize the flow of cyber
intelligence among federal agencies and between the private and public sectors.”
PwC convened leaders from the government, Fortune 100 and academics to
discuss and brainstorm a national public-private partnership to combat
cybercrime in April. Attendees helped draft proposed ISAO models and discussed
what government actions that could promote their creation and adoption.
You can see their related tweets here as well as their potential
models and the nuts and bolts of ISAOs � required protocols, trust-building,
creating real value and incentives for participants, government interaction,
liability issues, and reputation considerations.
Final
Thoughts
I often get asked to comment more on
the ups and downs of cybersecurity legislation, but after watching history
repeat itself multiple times over the past five years, I generally hold off.
I find commenting on new cybersecurity legislation is a bit like searching for
stories about Tim Tebow chasing his dream to play in the NFL.
You can love Tebow or hate him, but either way everyone keeps coming back for
more. And everyone seems to have an opinion on cybersecurity legislation –
whether you support more incentives to share data or advocate for more privacy.
I do believe that the success of recent bills demonstrates that legislation
will pass this year, with the cybersecurity bills mentioned above as main
ingredients in whatever compromises eventually emerge to be signed by the
president. Still, I have been wrong before, and I wouldn�t bet my house on
comprehensive legislation passing.
The same privacy groups continue to strongly fight these cyberbills on the
grounds that they are government surveillance programs. And while I have
privacy concerns as well, I am hopeful that a compromise will be reached. Nor
now, I will resist the temptation to put a timetable on when an agreement will
be reached.
Meanwhile I applaud the efforts of PwC and states like Virginia to get moving on implementing ISAOs now.
Back in April, Gov. Terry McAuliffe announced that the commonwealth of Virginia
is establishing the nation’s first state-level Information Sharing and Analysis
Organization (ISAO).
I encourage more state and local governments to follow Virginia�s example.
Lohrmann is Chief Strategist & Chief Security Officer of Security Mentor.
He works from his office in Okemos.