Cybersecurity vendor research has become one of the most crowded, fast-moving challenges in technology today. Thousands of vendors compete for attention, launching new products, pivoting business models, and merging to stay alive. For CISOs, investors, and corporate development teams, simply keeping track of who’s who has become overwhelming. Every week brings new funding rounds, shifting headcounts, and yet another product claiming to be a category leader.
This sheer noise creates risk. Teams waste valuable hours chasing scattered information across press releases, investor decks, conference brochures, and LinkedIn profiles — only to end up with gaps or outdated data. Choosing the wrong vendor can cost millions. Missing an emerging competitor can change an acquisition strategy. In short, cybersecurity vendor research has become a mission-critical challenge that few organizations have the time or tools to do well.
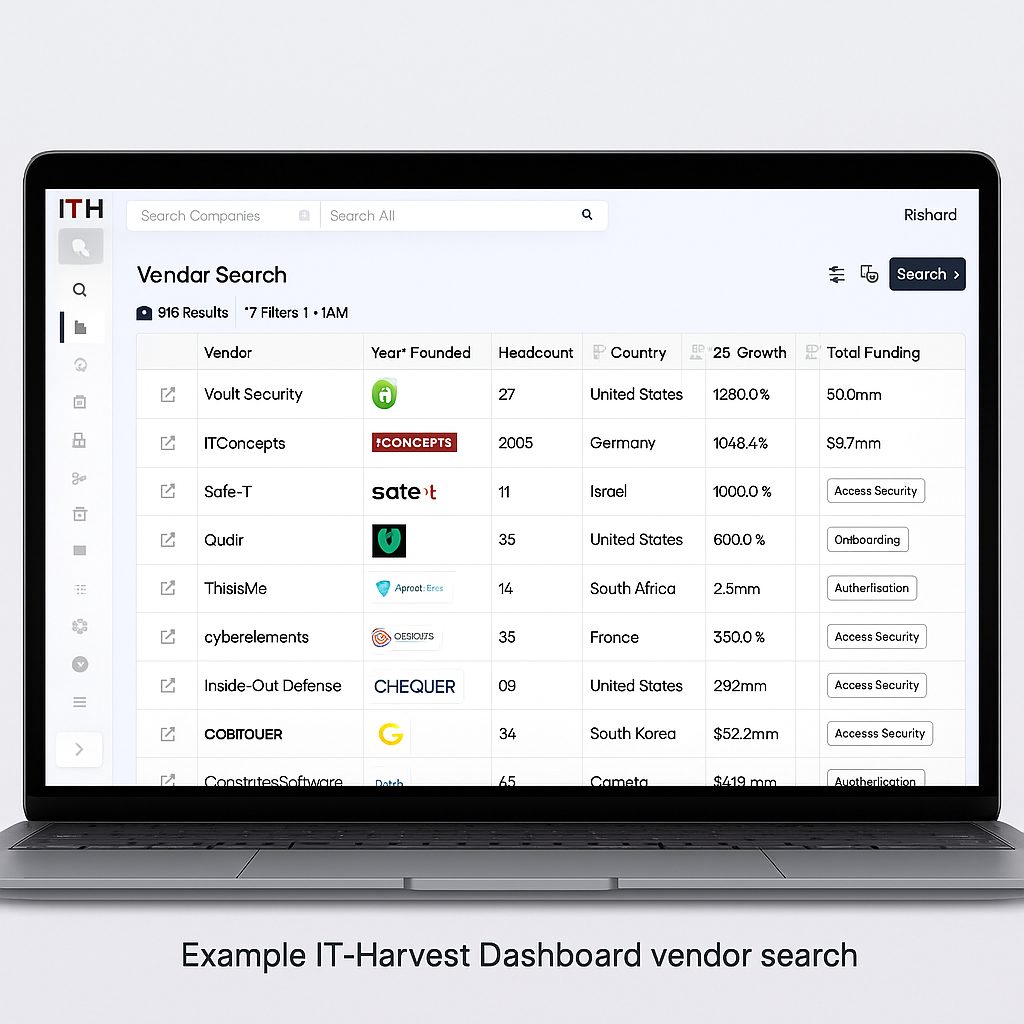
That’s exactly the problem IT-Harvest set out to solve. By centralizing reliable, continuously updated data on more than 4,500 companies and 11,000 products, the IT-Harvest Dashboard replaces guesswork with clarity. Searchable, filterable, and exportable, it gives decision-makers the structured intelligence they need to move faster and with confidence.
In our recent MITechNews segment on cybersecurity vendor research, Richard Stiennon introduced the IT-Harvest Dashboard and explained how it transforms scattered data into actionable insight. You can watch the full discussion below:
The Cybersecurity Vendor Research Sprawl Problem
What makes cybersecurity so challenging isn’t just the threats — it’s the endless stream of vendors claiming to stop them. More than 4,500 companies now compete in this space, offering over 11,000 products across every imaginable niche. Some are startups chasing their first round of funding. Others are global giants with sprawling product portfolios. Categories blur, buzzwords multiply, and what looked like a clear shortlist yesterday can be outdated by tomorrow.
For anyone tasked with cybersecurity vendor research, the result is a maze. Teams hop between news sites, analyst reports, investor updates, and LinkedIn searches, only to piece together fragments. Teams often overlook important players. Redundant products sneak into evaluations. M&A activity reshuffles the field overnight. The cost of missing a signal isn’t small — it can mean wasted budgets, stalled strategies, or failed acquisitions.
This vendor sprawl is exactly why IT-Harvest built its dashboard. Instead of treating research as a guessing game, it centralizes the industry’s most complete dataset and makes it usable — searchable by category, filterable by growth, and exportable for analysis. It takes chaos and turns it into clarity.
Who is Richard Stiennon?
Behind IT-Harvest is Richard Stiennon — one of the most recognizable names in cybersecurity analysis. For over two decades, Stiennon has tracked the industry’s evolution, chronicling how vendors rise, consolidate, and sometimes vanish. Executives, investors, and policymakers alike cite his work because it blends technical depth with business context.

His career spans influential roles: VP of Research at Gartner, where he guided global enterprise security strategies; CMO at Fortinet, helping to bring one of today’s leading security companies to market; and VP of Threat Research at Webroot Software. Along the way, he developed a reputation for cutting through hype and identifying the trends that actually matter.
Stiennon is also an accomplished author. His books — Surviving Cyberwar, There Will Be Cyberwar, and UP and to the RIGHT — have become required reading for understanding the geopolitical, military, and business dimensions of cybersecurity. Readers now trust his annual Cybersecurity Yearbook as a reliable reference guide, mapping the industry year by year.
Academically, he combines technical and strategic training with a BS in Aerospace Engineering from the University of Michigan and a Master’s in War in the Modern World from King’s College London. He’s been named a “Security Change Agent,” one of the “Top 50 Most Powerful People in Networking,” and a “Top Cyber Pro” for his contributions to the field.
All of this expertise comes together in IT-Harvest. Stiennon’s mission is to provide organizations with what he has spent his career building: clear, structured intelligence on an industry that often feels unstructured and opaque. For IT-Harvest subscribers, his decades of research are not just in books — they’re embedded in the dashboard itself.
Learn more at www.it-harvest.com or connect with Richard on LinkedIn.
What is the IT-Harvest Dashboard?
The centerpiece of IT-Harvest is its Dashboard — a living, breathing map of the cybersecurity industry. More than a directory, it’s an analyst-grade research environment that organizes the chaos of thousands of vendors and products into something usable and actionable. Updated constantly, it provides clarity on who the players are, what they sell, how they’re performing, and where the industry is moving.
Designed for decision-makers
At its core, the Dashboard is built for professionals who can’t afford to rely on guesswork. CISOs use it to build and defend vendor shortlists. Corporate development teams use it to spot acquisition targets before competitors do. Marketing leaders use it to benchmark their landscape and validate strategy. Investors use it to track portfolio companies and discover emerging opportunities. For each of these audiences, the Dashboard saves time, reduces blind spots, and injects confidence into high-stakes decisions.
Live, structured data at scale
What sets it apart is the depth of the data and the way it’s delivered. Instead of piecing together spreadsheets from scattered sources, subscribers log in to a single platform that contains structured intelligence on more than 4,500 vendors and over 11,000 products. The information isn’t static — IT-Harvest updates it continuously, unlike most annual reports. The Dashboard refreshes headcount trends, funding rounds, revenue estimates, competitors, and product details as they change, so users always see the current picture, not last quarter’s snapshot.
Analyst-grade clarity for cybersecurity vendor research
As one reviewer noted, the Dashboard gives users the power to “answer questions that would normally require the expertise of an entire analyst team.” That’s the promise of IT-Harvest: turning the overwhelming sprawl of the cybersecurity market into a single, navigable view that drives smarter choices.
Taken together, these capabilities make the IT-Harvest Dashboard more than just a research tool. It’s a living platform that delivers clarity, context, and confidence in an industry defined by constant change. For any organization serious about cybersecurity vendor research, it’s the difference between chasing fragments and seeing the whole picture in one place.
Who Benefits From Cybersecurity Vendor Research
The need for reliable cybersecurity vendor research cuts across nearly every corner of the industry. Whether you’re defending a network, scouting acquisitions, or tracking investments, the ability to separate signal from noise is mission-critical. The IT-Harvest Dashboard was built to give each of these groups a clear view of the market — without the wasted time and blind spots that come with manual research.
- CISOs and security architects: build data-backed shortlists, validate capabilities, and track supplier health over time.
- Corporate development teams: surface acquisition targets, monitor funding and growth, and map category trajectories before competitors spot them.
- Marketing and sales leaders: benchmark competitors, size categories, and plan presence at relevant conferences with confidence.
- Investors and analysts: watch portfolio performance, discover rising vendors, and quantify segment shifts with hard numbers instead of hype.
- Journalists and researchers: access verified, current data without manual scraping and guesswork.
Across these audiences, the outcome is the same: better decisions, faster. The IT-Harvest Dashboard levels the playing field by giving professionals at every level access to the kind of intelligence that once required a dedicated analyst team. In a market where being first with the right information can determine success or failure, that advantage is impossible to ignore.
A Cybersecurity Vendor Research Walkthrough
To see the power of the IT-Harvest Dashboard in action, imagine you’re part of a mid-sized enterprise tasked with finding a new identity and access management (IAM) solution. Traditionally, this kind of cybersecurity vendor research would take weeks — combing through analyst reports, browsing vendor websites, scanning conference agendas, and reading endless blogs. Even then, the list you build might be incomplete or already outdated.
- Log into the Dashboard and filter vendors by the IAM category.
- Apply criteria such as employee headcount, recent funding activity, and U.S.-based headquarters.
- Generate a shortlist of about a dozen vendors in seconds instead of weeks.
- Drill into each profile to compare headcount growth, revenue estimates, and health scores.
- Review product catalogs and see how each vendor stacks up against its closest competitors.
- Create a watchlist and set alerts so any change — new funding, product launch, or staffing surge — triggers an update for your team.

The result is a shortlist you can trust, backed by current data and clear context. What once felt like a scavenger hunt across scattered sources becomes a streamlined process that takes hours instead of weeks. And because the Dashboard updates continuously, your research doesn’t expire the moment you hit “save.” It evolves alongside the market, ensuring your team stays one step ahead.
What Makes IT-Harvest Different
Plenty of platforms claim to track cybersecurity companies, but none offer the depth, accuracy, and context of IT-Harvest. Where directories and one-off reports stop, IT-Harvest keeps going — delivering a living, breathing view of the entire industry. With coverage of more than 4,500 vendors and 11,000 products, it doesn’t just scratch the surface. It paints the full picture, from emerging startups to established giants.
What truly sets IT-Harvest apart is its combination of human expertise and data discipline. IT-Harvest standardizes and normalizes every entry for apples-to-apples comparisons — something you won’t find in scraped lists or static PDFs. The platform is continuously updated, so changes in headcount, funding, or acquisitions are reflected in near real-time. That means subscribers rely on current data, not stale intelligence.
“My goal with IT-Harvest has always been to give cybersecurity leaders the same depth of insight an entire analyst firm would provide — but in a way that’s fast, practical, and always up to date.”
– Richard Stiennon, Chief Research Analyst at IT-Harvest
And then there’s the context. IT-Harvest is led by Richard Stiennon, a veteran analyst who has spent decades studying this industry. His perspective informs how data is organized and prioritized, turning raw numbers into insight. That analyst DNA is embedded in the Dashboard, giving users the benefit of years of research methodology every time they run a search.
To push the advantage even further, IT-Harvest integrates AI-powered assistants. The Analyst Assistant delivers instant intelligence on vendors — from funding history and growth rates to competitive positioning. The Architect Assistant does the same for products, helping teams cut through marketing noise and focus on what really matters. This blend of curated human insight and machine-speed guidance is what makes IT-Harvest not just useful, but indispensable.
Earlier this year, MITechNews reported on IT-Harvest’s launch of AI assistants, showing how the Dashboard now blends human analyst expertise with AI-driven guidance to deliver even deeper vendor and product intelligence.
In short, IT-Harvest isn’t another research tool. It’s the first platform built to give security leaders, investors, and strategists the same level of visibility an entire analyst firm would provide — but in one place, at their fingertips, and always up to date.
From Constant Change to Cybersecurity Vendor Research Clarity
The cybersecurity market doesn’t stand still. Vendors merge, products pivot, and funding reshapes the competitive landscape almost overnight. A quarterly report is out of date by the time it’s published — and decisions based on old information can be costly. That’s why IT-Harvest was built to update continuously, reflecting the live state of the market so leaders can act with confidence, not guesswork.
The best way to understand this difference is to see it firsthand. A short demo shows how quickly the Dashboard can turn scattered research into clear, actionable intelligence.
Cybersecurity leaders are already weighing in on this topic. Don’t miss the chance to add your voice to the discussion.
See the conversation on LinkedIn and share your perspective.
Visit dashboard.it-harvest.com, submit the form, and mention code 919 for an expedited response. In 15–20 minutes, you’ll see how filters, exports, and watch lists fit seamlessly into your process — and why constant clarity is now possible in a market defined by constant change.